Must-Know Common Law Firm Cybersecurity Issues in 2025

The Big Picture: 2025 in Cybersecurity for Law Firms
35% of small business leaders believe their organization is not resilient enough to withstand the impact of a cyberattack. And unfortunately, 90% of organizations are exposed to at least one path of cyberattacks—including increasingly sophisticated phishing, fraud, and ransomware attacks.

In fact, 90% of IT and Security executives globally have already reported falling victim to attacks in the last year.
In 2025, law firms will be challenged by many evolving, changing, and intensifying threats. Attackers will continue to be empowered by AI, which allows them to magnify the impact of malware, commit fraud more easily than ever before, and much more. Law firms will also be subject to a variety of other targeted attacks that seek access to sensitive client and company information, hoping to exploit some of the large volume of personal data housed by law firms.
The consequences of these attacks can be extremely serious from a legal, regulatory, and reputational standpoint. Data breaches can cause up to 60% of mid-sized law firms to shutter within 6 months of a successful breach.
We share these statistics to help educate law firms, not to cause fear or panic. Though the magnitude of cybersecurity attacks can be severe, and the data is certainly alarming, the best defense is to stay calm and be proactive. Focus on what your law firm can do to protect yourself today.
We’re here to help you discover those next steps and share our expertise in keeping your law firm safe.
Zooming In: What Law Firms Should Know Today
Some cybersecurity issues are especially common in the legal industry, showing up across a wide variety of small to mid-sized law firms time and time again. By educating yourself and your team about these risks, your law firm can begin to bulk up your “security posture,” AKA your standing against cybercriminals, and stay on guard against threats.
Below, we’re sharing the most common cybersecurity issues taking place right now at law firms around the world and some quick tips to help your firm stay safe.
Though these practices may seem small in the face of large threats, simple adjustments add up to a big impact. Every small action you take today helps strengthen your organization for the future ahead.
#1: Poor Password Hygiene and MFA Practices
Gone are the days of passwords on Post-its—and no, you can’t use your pet’s name, either.
While most folks are up to speed on password best practices– like secure password keepers, biometrics (think Apple Face ID &ID & Android Face Unlock), and unique passwords for each platform—not everyone takes these guidelines as seriously as they should.
Law firms often struggle to enforce strong password policies and multi-factor authentication (MFA), making it easier for attackers to gain unauthorized access. These practices are like individual locks on your front door—the more of them, the better quality they are, and the more complex they are to open, the harder it is for intruders to enter.

Law firms should create cyber policies that include password hygiene and multi-factor authentication clauses and ensure that they are followed. Though it can be difficult to enforce these policies, there are a few practices that can help, including:
- Required password changes after an incident
- Documented policies that employees must sign
- Cybersecurity awareness training and seminars
- Setting organization-wide mandatory MFA requirements for each application
- Access to password management apps like Keeper
- Access to MFA apps like Microsoft Authenticator or Duo
#2: Lack of Preparedness for Phishing Attacks
From texts and emails to spam phone calls and letters, you’ve probably seen phishing attempts in action many times. Law firm employees are common targets for phishing scams, which are cyberattacks that trick real people into giving up sensitive information or access to programs, applications, and assets. Sadly, employees may not always recognize or prevent these attacks.
This issue arises due to a lack of education and awareness about phishing attempts—and nowadays, scammers are really good at impersonating legitimate people and organizations, making education all the more important. Many studies state that around 90% of all cyberattacks begin with phishing—and for many law firms, the gap in employee knowledge is the weakest link. Yet, regular security awareness training and phishing simulations are often a low priority at many law firms, leaving employees ill-equipped to handle cyber threats.
Because law firms handle a high volume of sensitive client and organizational data, they make a perfect target for hackers looking to steal client data to commit identity theft, orchestrate ransoms, or even sell identities on the dark web.
AI has empowered phishing artists to spoof emails, voices, and even videos of real people in order to impersonate them more accurately and convincingly. The use of AI in cyberattacks has gotten so intense that Microsoft recently issued a warning, stating they have “stopped $4 billion worth of fraud attempts, blocked about 1.6 million fake bot signups every hour, and rejected 49,000 fake partnership requests. This shows how common online fraud has become, especially as scammers use AI to trick people more easily,” reports ExtremeTech.

Awareness and education are your best defense against even the most advanced phishing scheme.
You can help strengthen the safety of your people and organization through phishing awareness training and the spread of up-to-date resources about phishing. Sharing this knowledge with your team helps them stay on their guard against bad actors. Employees should learn to spot and report phishing schemes and how to properly handle potentially dangerous emails and phone calls to prevent any intrusions. Be sure to train your team thoroughly and regularly to stay on top of evolving threats—a professional service like Huntress Managed Learning can help you accomplish this.
#3: AI and Emerging Risks
Hackers may be using AI to advance their phishing attempts, but that’s far from the only security risk AI presents.
It can be tempting to dive right into new technology offerings, but in the case of AI, buyer beware. As law firms jump on the newest technology trend, artificial intelligence, it becomes increasingly important to understand the risks AI opens the firm to.
AI is introducing law firms to new and existing risks due to unclear governance and oversight. Many times, a firm will implement an AI tool without first consulting or creating proper guidelines and controls. This allows AI systems to inadvertently compromise sensitive data or make biased decisions. Here’s what that means:
Studies show that AI can be biased based on human biases, far from the neutrality many users expect from a machine. This can land law firms in a poor position regarding hiring, research, and internal practices. In addition to its bias, AI can get facts wrong, and even make things up, a phenomenon known as “hallucination.” In one notable 2023 case, a lawyer using AI to research precedent for a case inadvertently submitted at least six completely fabricated court cases shared with him by the AI tool.
When employees utilize AI without proper guidelines, not only do they provoke the reputational risks associated with bias and incorrect information, they also open up direct gaps in the law firm’s cybersecurity. Because AI is fed human data in order to “learn,” it can retain sensitive information that may be entered by employees’ prompts—a recent study on GenAI leakage showed that 8.5% of all employee AI prompts contained sensitive data.

Furthermore, states CSO online, “Harmonic, which analyzed tens of thousands of prompts to ChatGPT, Copilot, Gemini, Claude, and Perplexity during Q4 2024, found that customer data, including billing information and authentication data, accounted for the largest share of leaked data at 46%[…] Employee data, including payroll data and personally identifiable information (PII), accounted for 27% of sensitive prompts, followed by legal and finance data at 15%.”
Hackers can then penetrate the AI tool and extract the data employees enter, gaining access to numerous client and proprietary business data points and exploiting them for fraud, ransom, sale, and more.
It’s important to evaluate your law firm’s cybersecurity maturity prior to adopting any emerging technology tool, and to evaluate the specific risks against your law firm’s risk tolerance to determine if the solution is a good fit. To properly manage the tool, user policies and governance must be in place before access is granted to employees. This can look like:
- Standards and policies enforced by IT
- Ongoing risk management conversations and practices
- Continued research and staying up to date on evolving threats
- Regular IT audits
#4: No Remediation Plans for Emergencies
It’s better to be overprepared than underprepared, especially when it comes to cybersecurity. Even when a law firm takes proactive measures to prevent a breach, they should also have a clear and comprehensive plan for responding to an incident if it should happen.
Unfortunately, many law firms are not prepared for an incident or breach. They do not have clear frameworks and plans for locating, containing, responding to, or remediating threats. This lack of planning can create panic, short-sightedness, and misguided decision-making if they do find themselves in the midst of a cyber incident.
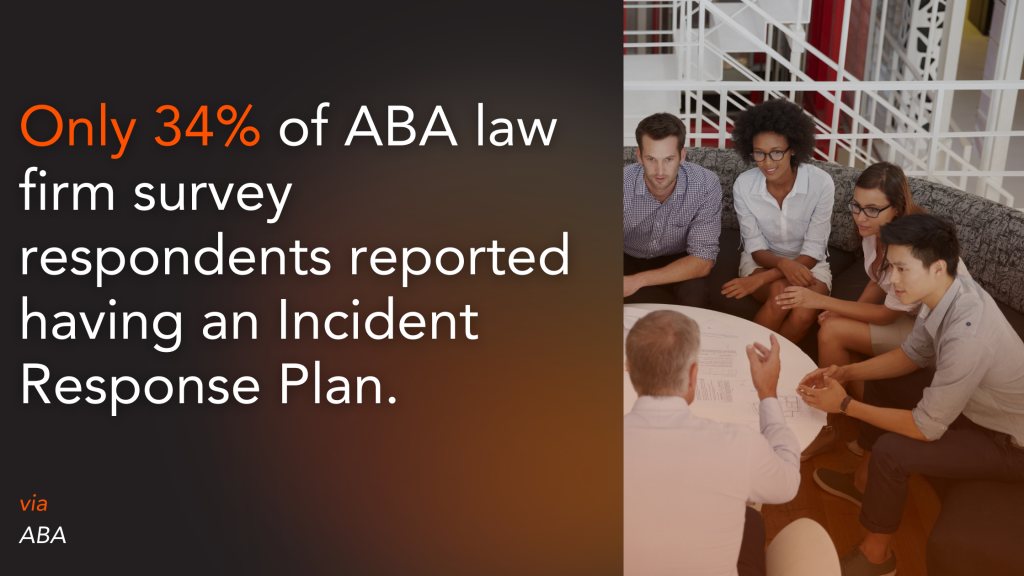
Lack of Incident Response Preparedness
Most law firms lack a comprehensive incident response (IR) policy—often their plan is to open a ticket with their IT department or technology partner and hope for the best. There are typically some assumptions—that the IT manager on-site can handle the threat or will know who to call to fix it, that they aren’t a valuable target to hackers and therefore won’t experience an incident, that their technology partner can instantly stop an intrusion… the list goes on, but these assumptions are too often false.
Worse yet, some law firms don’t have a robust on-site IT department and also aren’t engaged with a cybersecurity partner, so if an incident does occur, they may not discover it—let alone contain and respond to the threat—before it’s too late. Typically, these firms engage a third-party security and forensics vendor at the time they discover the incident, and by then, the damage is already done. Without having established a relationship with IT vendors prior to the incident, the decision-making and action-taking processes can be delayed or misguided, with a lower level of service than the situation requires.

Implementing a robust IR plan is crucial for quick and effective responses to security incidents. As per NIST guidelines, an IR plan should contain:
- A defined incident response team with roles and responsibilities outlined
- Roles to determine the nature of the threat and its validity
- A formal process for documentation of the incident
- Guidelines for prioritizing the threat should multiple incidents occur
- A process and tools for notifying the proper parties of the incident
- A predetermined plan and tools for containing and eradicating the threat
- A recovery plan
Inadequate Backup and Disaster Recovery Plans
While many law firms use data backup services, they often lack a clear plan and understanding of the steps needed during a restore scenario. A well-defined disaster recovery plan (DRP) is essential to minimize downtime and data loss.
A disaster recovery plan and an incident response plan are not the same thing, despite some overlap—an incident response plan focuses on handling the incident in real-time, whereas a disaster recovery plan focuses on restoring lost data and service after a successful breach or attack occurs. A law firm should have both plans in place to ensure their safety.
“Disasters” aren’t always the result of cyberattacks, although they certainly should be included in an assessment of threats to your law firm. Disasters can be caused by issues like:
- Malware, ransomware, and DDoS attacks
- Natural disasters and severe weather
- Power outages and maintenance
- Data breaches
- Loss of mission-critical service from a third-party
- Data center outages and damage
- Bugs and system failures
- And more
These issues are often out of the hands of law firms and technology partners and can’t always be prevented—even by the most resilient of technology. If your law firm is not prepared, this can lead to a magnitude of data loss and make recovery difficult to achieve.
In order to draft a proactive DRP, your firm should consider the following:
- What risks are most likely to impact your law firm
- Roles and responsibilities for the DR team
- Fast and efficient steps for responding to each type of emergency scenario
- Instructions for restoring key services
- Contact information for IT professionals and partners who will need to be involved in disaster recovery efforts
In addition to having a plan on hand, it’s critical for law firms to think ahead about preventing data loss through a backup solution. Even data hosted on the cloud can be wiped out by an attack, and even data hosted in filing cabinets or servers can be destroyed in a natural disaster. So, be sure that your backup practice includes multiple methods of data hosting and that your backup services include multiple methods for retrieving data from different sources.
#5: Outdated Applications and Insecure Configurations
You can’t teach an old dog new tricks—and you can’t expect old technology to support new tools and security standards.
Despite new and emerging technologies becoming available, law firms are often still using legacy technology, a term for older and less efficient hardware and applications that can’t keep up with modern productivity. Older computers, phones, and systems tend to create security issues, as they may not be compatible with the newest and most secure software and may be behind the curve on threat protection as cybercrimes evolve.

While the technology itself presents issues, so do the configurations this technology exists in.
Technology asset configuration refers to the arrangement of hardware, tools, and solutions. It includes settings and customizations, including security and productivity settings, as well as the technology’s place in the overall tech stack. Many law firms use outdated applications and insecure asset configurations, which increase security vulnerabilities.
Major security risks stem from a lack of application management, application sprawl (too many applications that become unmanageable), and challenges in patching or hardening legacy hardware and software. Legacy items are typically incompatible with modern updates after a certain point, meaning they can’t be patched or hardened to protect against evolving threats. Firms also seek new solutions to solve issues with their legacy technology, adding new applications and solutions to their technology instead of addressing the root cause—the older software and hardware itself.
As cybersecurity threats grow in number and the cost to businesses reaches new heights, now is the right time for law firms to say goodbye to outdated technology.
Modernizing IT infrastructure can be made easier with the help of a technology partner. It’s important to find an advocate who can help use business information and data, along with their technical expertise, to help your firm take this step into the future.
By modernizing your technology with new hardware, software, and solutions, you can be sure that your firm achieves the modern pace of productivity and remains in the safest possible standing amidst cyber threats. The right partner makes the switch easy and headache-free.
What’s Next? Getting the Help Your Law Firm Needs
Strategic Technology Solutions is a technology business partner especially dedicated to keeping law firms safe. We work exclusively with legal professionals to keep their law firms safe with modern, secure technology. Our experts help law firms craft incident response and recovery plans and can serve as knowledgeable, level-headed point of contacts in an emergency, and we use state-of-the-art security solutions to prevent and respond to the threats law firms face daily.
STS is eager to educate our clients to help them use technology with confidence. We can help your law firm educate and train employees to prevent human error and social engineering-based risks, while also providing peace of mind to your law firm leadership knowing that their business is protected from internal and external threats.

An Easy Next Step – Free Offer: Security Vulnerability Scan
We’re offering law firms a Free Security Vulnerability Scan, a simple scan of your technology systems to determine areas of vulnerability and help create simple, swift action steps for protecting your firm today.
Get the clarity you need at zero cost or obligation. Click the button below to learn more or request a scan.