Are you prepared to defend your law firm against cyberthreats?

You’ve heard of cybersecurity, but have you heard of cybersecurity maturity?
Probably not, because most Managed IT Services (MSPs) providers aren’t talking about it nor are they managing cybersecurity as the discipline it truly is. Cybersecurity maturity is a comprehensive, multidimensional approach that reduces your firm’s overall cybersecurity risk.
It’s time you knew the difference so that you can informed security decisions on whether to take preventative action or assume the risk for your law firm. We’ll walk you through everything you need to know about cybersecurity maturity below.
What is cybersecurity maturity?
First and foremost, cybersecurity maturity is a discipline. It requires persistent, ongoing, and repeatable actions to protect your firm against the continuously evolving cyber threat landscape.
Specifically, cybersecurity maturity refers to how well your business integrates security safeguards throughout your operations and stages of growth.
Gone are the days when cybersecurity was a one-and-done solution against malicious actors. There is no one tool, strategy, or policy that is effective enough to withstand the onslaught of today’s threats.
You need a comprehensive cybersecurity maturity program and a way to track and measure your security actions and behaviors. In order to track your security progress, you’ll need to use a cybersecurity maturity model.
What is a cybersecurity maturity model?
Maturity models provide a framework and score against which you can measure and track the impacts of your security efforts. Though there are many models to choose from, the best-known models include the National Institute of Standards and Technology (NIST), Control Objectives for Information Technologies (COBIT), Project, Program, Portfolio Management (P3M3), Information Security Management (2MISM), and ITScore. The most important aspect of any model is that you use it consistently for best results.
At STS, we combine the NIST, cybersecurity maturity model and the Center for Internet Security’s (CIS) best practices. It’s beneficial for law firms to use the NIST framework because most industry regulations pull their controls and audit you from this particular model. This makes it easier for law firms to attain and remain in compliance.
What is the NIST cybersecurity framework?
According to NIST, the framework is “a voluntary guidance, based on existing standards, guidelines, and practices for organizations to better manage and reduce cybersecurity risk.” It’s designed to help companies recognize, govern, and lower their cybersecurity risk while safeguarding their networks and data. Using this framework helps firms make the right decisions on where to invest your firm’s time and money in cybersecurity.
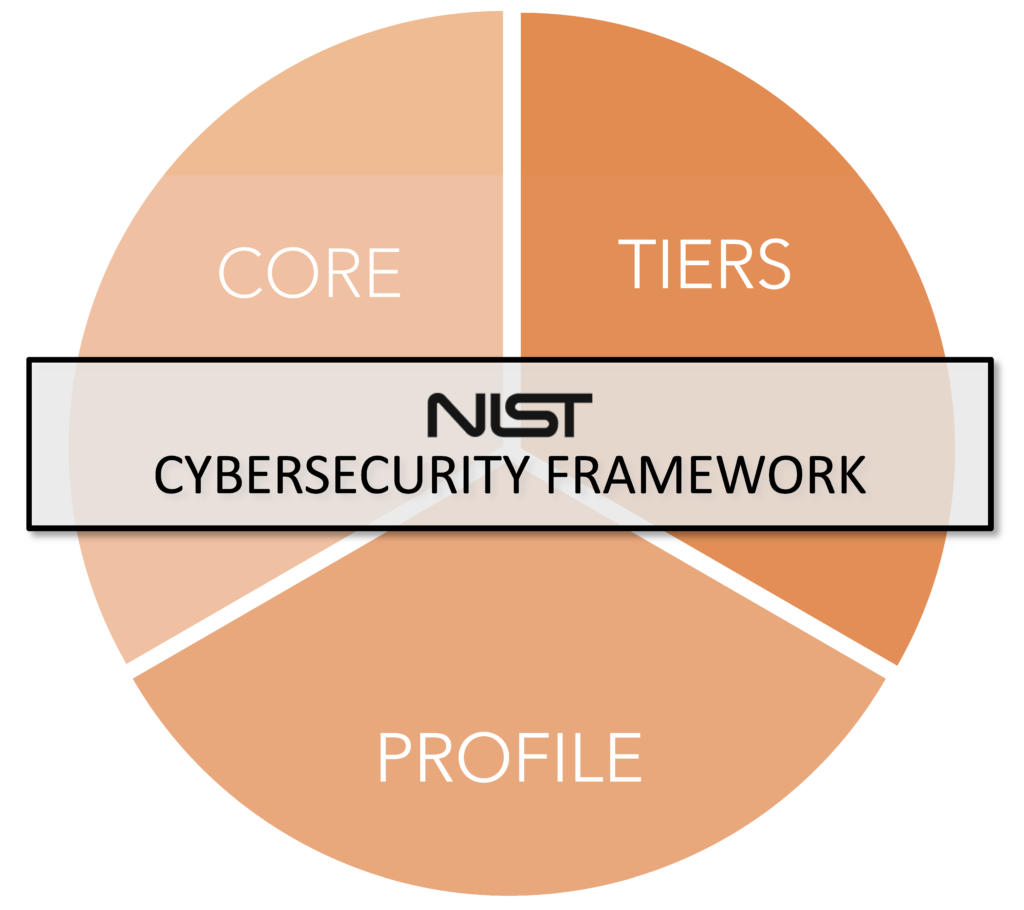
This framework has three main components: Core, Tiers and Profile.
The Framework Core
The Core is a set of desired cybersecurity activities and outcomes that are organized into Categories and aligned to Informative References, which are specific standards, guidelines and practices. The Core is made up of three parts, Functions, Categories, and Subcategories. It also has five high level functions: Identify, Protect, Detect, Respond and Recover.
These five functions are central to managing your firm’s cybersecurity risk. Each function corresponds to specific cybersecurity tools, strategies, and processes that can be put to work in your business. You can see below that the five functions live on an approach continuum ranging from proactive to reactive actions. Most firms focus only on reactive efforts when all firms need both proactive and reactive functions to reduce their risk successfully over time.
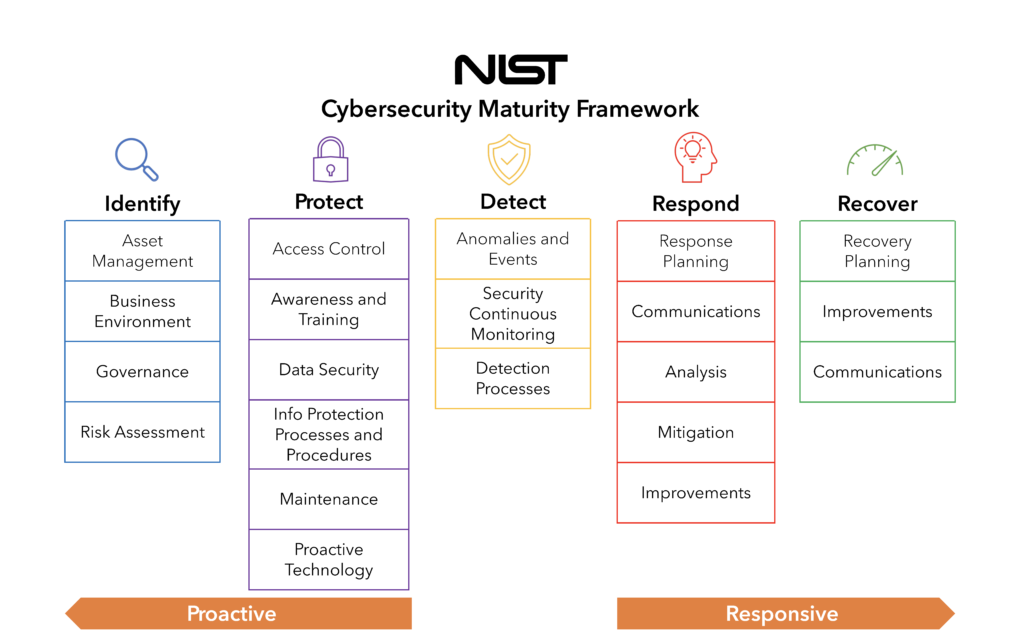
Learn more about the five functions here.
Implementation Tiers
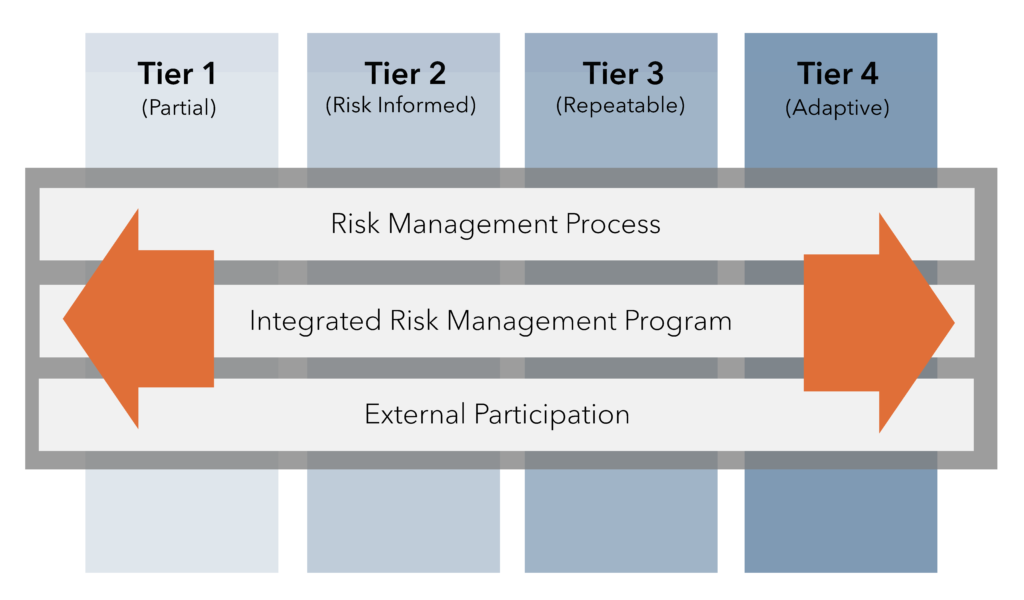
Tiers describe how well your firm’s cybersecurity risk management practices embody the characteristics (Partial, Risk Informed, Repeatable, and Adaptive) in the Framework. The Tiers range from 1 to 4 and represent an increasing level of sophistication in cybersecurity risk management practices.
Though Tiers are different than your maturity level, it’s helpful to identify your desired Tier level. Selecting your Tier takes different variables into consideration. These include your current cyber risk management practices, the current cyber threat environment, legal and regulatory requirements, information sharing practices, business objectives, and organizational constraints.
Learn more about Implementation Tiers and their levels here.
Profiles
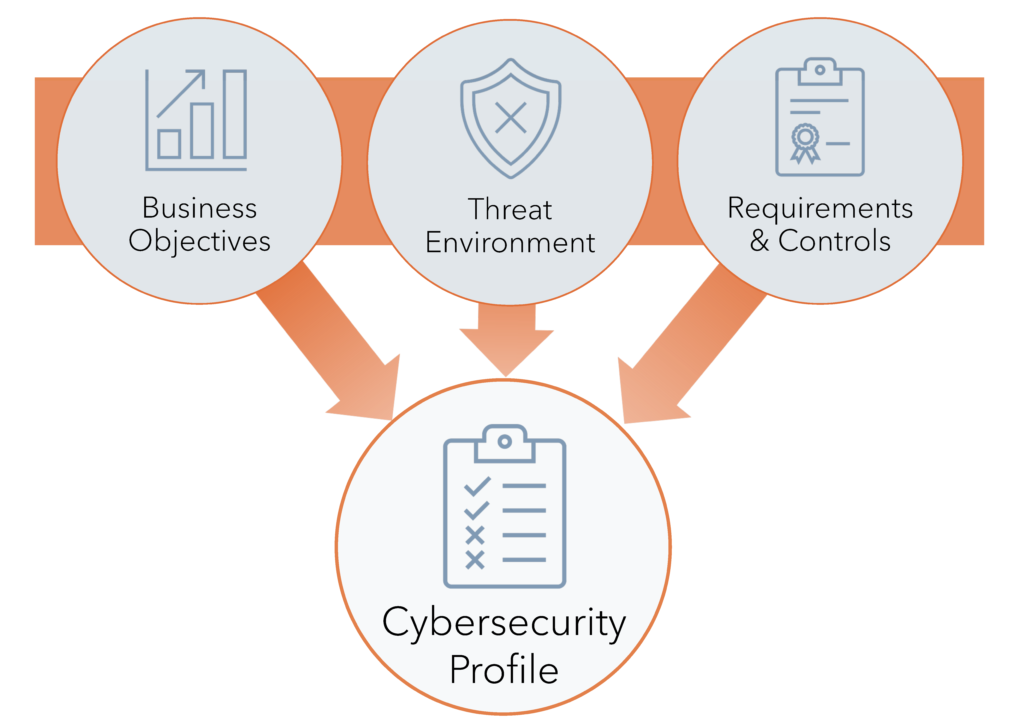
The Framework Profiles align the Functions, Categories and Subcategories with your firm’s requirements, resources, and risk tolerance. Profiles are instrumental in creating a roadmap that aligns your cybersecurity risk management with your firm’s business goals, legal and regulatory requirements, industry best practices, and your risk management priorities. Depending on the complexity of your company, you may have multiple profiles.
Learn more about Profiles here.
In addition to this maturity model, STS uses the CIS best practices whose controls are based on the NIST cybersecurity framework.
What are Center for Internet Security (CIS) best practices?
Using the NIST framework as a reference, CIS prioritized 18 critical security controls that when implemented can help protect companies from cyber threats and prevent up to 98% of reported breaches.
Here are the 18 controls:
Take all gathered info and measure against these 18 control groups (within are a subset of controls that STS verified were in place nor not).
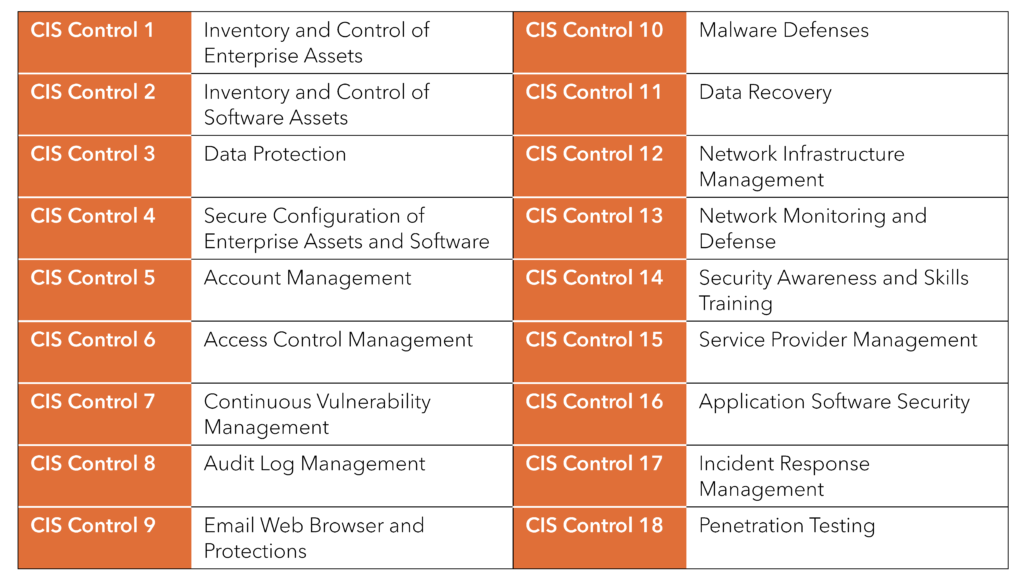
Learn more about each security control here.
How do NIST and CIS, together, help drive a robust cybersecurity maturity program?
By combing the NIST Framework with the CIS best practices, firms can help establish their baseline and track their security maturity progress.
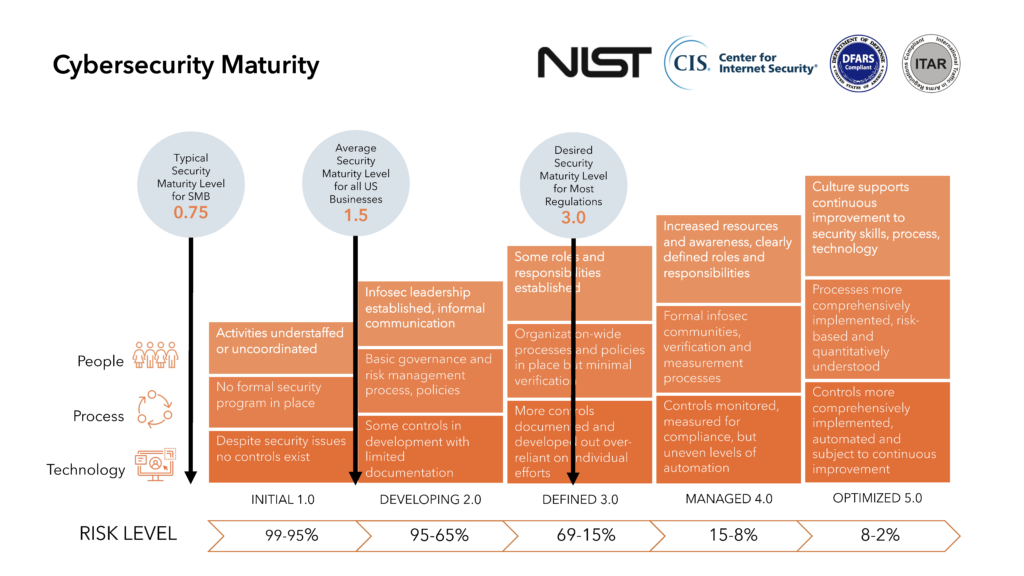
Below is a graphic that maps out the five levels of NIST’s security maturity model from Zero 0.0 to Optimized 5.0. As your maturity levels increase, you decrease your firm’s percentage of risk. Overlaid on the figure below are three different benchmarks representing small and medium-sized businesses (SMB), US businesses (overall) and the desired level to meet regulatory requirements:
- Typical Security Maturity Level Score of SMB: 0.75
- Average Security Maturity Level Score for all US Businesses: 1.5
- Desired Security Maturity Level Score for Most Regulations: 3.0
How do you measure your cybersecurity maturity level?
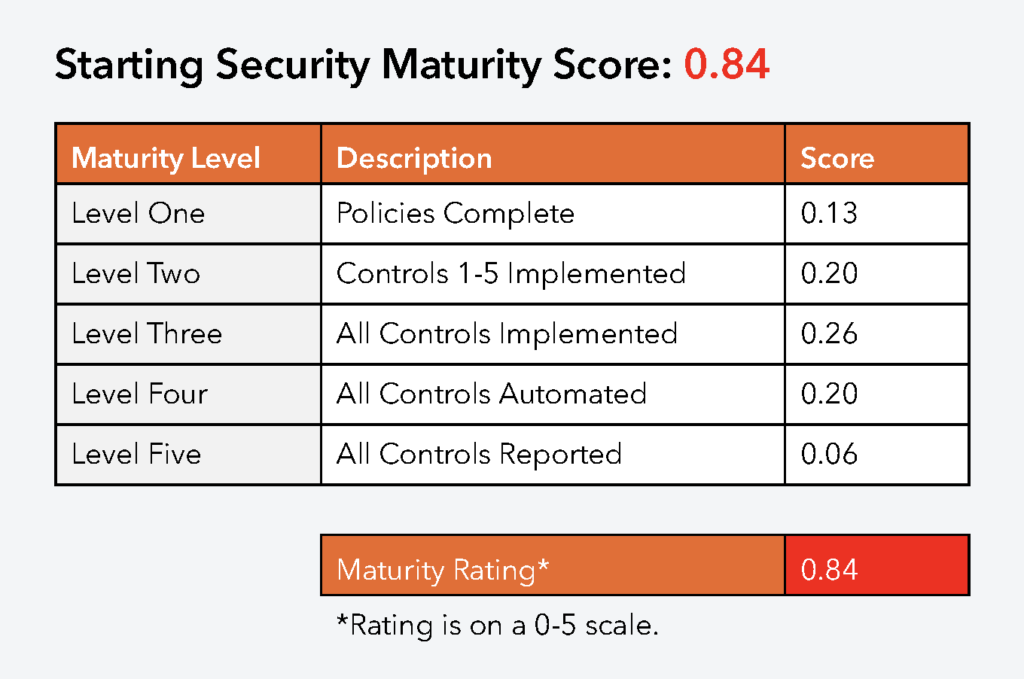
Your cybersecurity maturity level goes hand in hand with your score and depends on the given maturity model. Different models use their own distinctive frameworks, naming conventions, and scoring. Overall, your maturity level and score are a measure of how prepared your firm is to meet cyberthreats within the context of your business over time.
Get a Security Maturity Level Assessment.
Ready to leverage technology to increase your productivity, protection, and profitability? Contact us here to get started with an IT Assessment.