Cybercriminals are coming for your law firm…are you ready?

The truth is that threat actors are probably already in your IT systems, quietly gathering intelligence on your greatest security vulnerabilities. Their preferred entry into your IT systems is through your firm’s inbox.
In fact, according to the FBI’s 2021 Internet Crime Report, phishing email attacks increased by roughly 1,100% from 2017 to 2021. Its popularity among malicious actors is a testament to its efficiency. The bar graph below maps out the top 5 cybercrime types while clearly illustrating the rising charge of phishing campaigns.
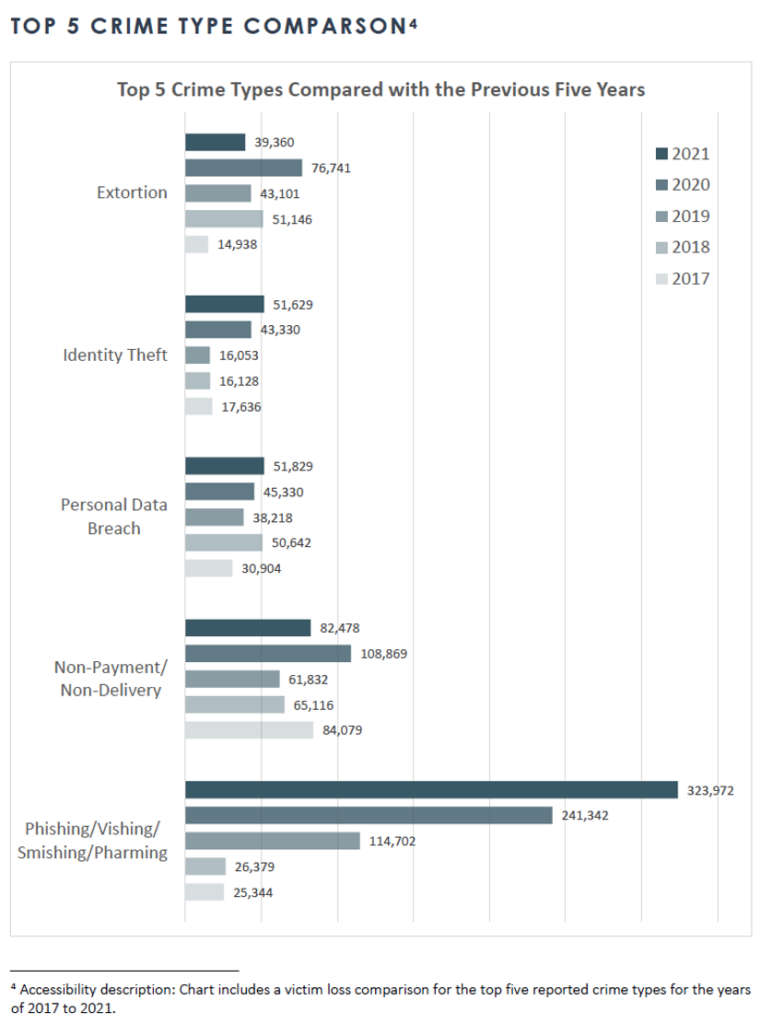
Phishing emails among other threat tactics can be difficult to discern from real emails. This is one of the many reasons that most law firms don’t know they’ve already been hacked. These threat actors strike like a silent heart attack. Though they leave traces of their activities in their wake, you will never know unless you’re purposely scanning and monitoring your systems.
Law firms, especially small-to-medium-sized firms, are attractive cybercrime targets for multiple reasons:
- Privileged and confidential data are extremely easy for threat actors to monetize
- Outdated, ineffective cybersecurity controls and defenses
- Data sensitivity and weak security measures, when combined, create a “backdoor” to access large corporations via their law firm
That last one is the scariest. Cybercriminals are not only keen on taking you down for a handsome reward but will leverage your defenses to go after your biggest, most valuable clients.
We don’t need to point out that the ramifications of a firm breach are huge.
The best path forward is to find and vet the right managed IT Services and cybersecurity partner and to invest in a robust cybersecurity program as if your life depended on it. Because it does. A major breach of this nature could shut you down for good. Losing your most valuable clients, the “salability” of your firm’s reputation, plus the costs of a breach cleanup (remediation, lawsuits, and regulatory fines) can be astronomical. Enough to take down your business.
Lawyers aren’t known forengaging in high-stakes, risky behaviors when it comes to their business. Yet, not investing in a disciplined cybersecurity plan is like playing roulette with your firm.
Leaving the potential of a firm breach up to chance is not—and never will be—in good odds.
The challenge is that finding and vetting the right technology partner and security program takes time—and it should. It’s one of the most important investments you’ll make to support the success of your firm.
However, you need to augment your cybersecurity now. While you’re looking for your next IT partner, be sure to implement the following security recommendations immediately.
Write and implement a Password Policy.
This policy outlines specific, best practices to follow for the creation and use of strong passwords. It includes directions on how to generate complex and unique passwords. In addition, the policy prohibits harmful password habits such as reusing passwords across home and work accounts. Another important component of a password policy is to implement a password manager. The primary benefit of a password manager is that it alleviates the pain of having to remember unique and complex passwords, thereby encouraging greater adherence to your policy.
Turn on Multifactor Authentication (MFA) for all your systems.
MFA adds another security layer around your password logins because it requires the user to provide another form of authentication (pin, smartphone, voice recognition, etc.). It’s an effective backup in case company passwords are stolen. To be effective, be sure to enforce MFA on every system that is accessible to the internet. In addition, do not allow legacy authentication as this increases your security risk. Be aware that while MFA is extremely helpful, it can still be bypassed.
Unfortunately, there is no one tool or strategy that can address all your firm’s security risks. This is where a multi-layered cybersecurity program comes in handy.
Use your Microsoft Office 365 Secure Score portal.
This portal is a security analysis tool included in your O365 package. Its primary function is to help you understand and use all O365 security features. Be sure to learn how it works and then use it.
Turn on Office 365 Unified Audit Logging.
This Audit Logging feature is also in your O365 package. However, it’s turned off by default. You’ll need to go in and turn it on. Its function is to track and monitor all user activities. These activities include reporting, deletions, shares, downloads, edits, reads, and more across all your O365 services. This feature allows you to customize your notifications so that you can be alerted for only specific activities. This is a great way to be in the know when suspicious activities are identified on your IT systems.
Be vigilant of software updates (patches).
Software companies regularly release patches for their product. These patches can include new features, bug fixes, or security updates (or a combo of all three items). Security updates are becoming increasingly more common because of the constantly changing nature of cyber threats. Be sure to track how you’ll be notified when a new patch is available for your existing software. It’s critical that you implement the patch immediately to avoid exposing your law firm to exploitable vulnerabilities.
What could happen if I don’t follow the above steps?
Your risk of being breached is near 100%. Chances are you’ve already been compromised; you just don’t know it.
Though there are things that you can implement now, these are just a bare minimum. To ensure that your IT infrastructure and systems stay protected, you’ll need a comprehensive, multi-layered cybersecurity program.
To choose the right cybersecurity program for your firm, you need to know where your risk lies today. To find out, sign up for our security maturity level assessment. This assessment will give you an in-depth understanding of your current security risks and vulnerabilities. You’ll leave with a customized cybersecurity roadmap on how to best protect your firm today and into the future. Contact us to get started with this assessment.